Have you ever wondered how many credit cards are in the world? According to rough estimations, almost 3 billion, and this number continues to grow. Unfortunately, the number of fraud cases keeps on growing, too. In fact, gross card fraud losses globally are projected to exceed $35 billion by 2025.
However, in 2019, the share of fraud in total card transaction volume started to decrease. If in 2018 fraud accounted for 6.86¢ of every $100 of total volume, a year later, it reduced to 6.78¢. For now, there are no calculations for 2020, but let’s hope the trend continues.
One of the key factors making it possible is the industry’s joint efforts to enhance card transactions security, reflected in PCI DSS.
In this article, we’re going to deep dive into PCI DSS meaning, history, requirements, procedures, and costs.
What is PCI DSS?
First of all, let’s answer the most common beginners’ question: what does PCI DSS stand for? The abbreviation is for Payment Card Industry Data Security Standard.
PCI DSS is a set of requirements for merchants created by American Express, Discover, JCB, Mastercard, and Visa to ensure the safety of card payments, prevent fraud, and secure cardholders’ data across the world. It applies to everyone who accepts or processes payment cards.
There are four levels of PCI DSS compliance depending on the number of card transactions business processes annually. Level 4 is for those processing less than 20,000 transactions, Level 3 — up to 1 million transactions, Level 2 — up to 6 million, and Level 1, the strictest level of compliance — more than 6 million transactions.
PCI DSS evolution
The first version of PCI DSS was created in 2004 when major card brands joined forces to design a unified digestible Standard instead of separate policies each of them have had in place before. They also formed the Payment Card Industry Security Standards Council, keeping PCI DSS up-to-date since then.
This way, PCI DSS 2.0 included some clarification of the requirements and emphasised the importance of data scoping and log management.
In its turn, PCI DSS 3.0 highlighted the need to turn security maintenance into daily work and appropriately educate personnel dealing with payment data.
At the time of writing, 3.2.1 is the PCI DSS latest version, with PCI DSS 4.0 scheduled for release later this year. However, industry experts predict that the 12 fundamental requirements we’ll take a grasp of in the next section won’t change significantly.
A gist of PCI DSS requirements
The PCI DSS security standards are organised into six categories that the document refers to as “control objectives”.
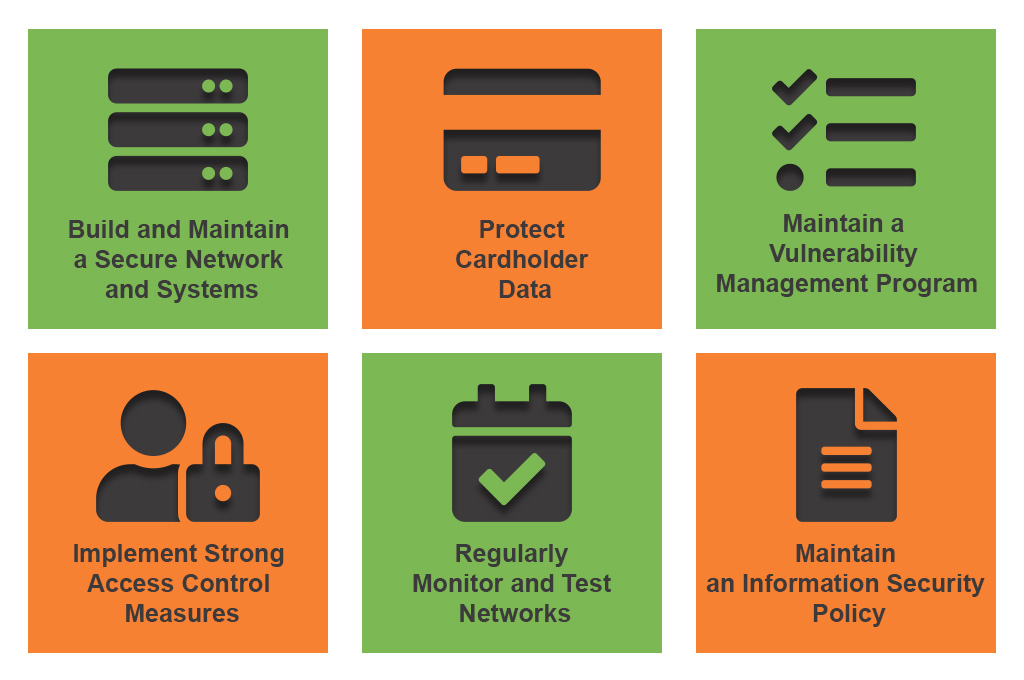
These six categories include certain sub-requirements that vary from version to version. However, 12 high-level requirements are still in place since the inception. They’re considered to be core principles of PCI DSS and are listed on the official Payment Card Industry Security Standards Council website.
12 core PCI DSS requirements explained by Ikajo
1. Having a network firewall in place.
It can be a software, hardware solution, or web application that you can configure to restrict unwanted incoming and outgoing network traffic. It’s the first line of defence to a network and is a must for a secure payment card environment. Businesses often neglect tailoring firewalls to their unique conditions, a mistake that relates to the next PCI DSS requirement.
2. Avoiding using default settings and passwords.
You can’t guarantee cardholders data security if you ignore your business specificities and use default parameters when setting up a payment environment. Needless to say, using default passwords is the worst thing one can do in terms of security. PCI DSS actually contains specific password requirements: 7+ characters, including letters and numbers, changed every 90 days etc.
3. Safe cardholders’ data storage.
All the cardholders’ data must be stored in an encrypted format and a protected environment.
4. Encrypted transmission of cardholders’ data.
Hackers frequently target the data on its way from point A to point B, so PCI DSS highlights that the transmission of data via open, closed, private, or public networks should be encrypted.
5. Using the latest antivirus software.
Regularly update your antivirus programs to ensure protection from emerging threats.
6. Developing and maintaining secure systems and applications.
Assess the risks before implementing new equipment or software and apply patches when needed.
7. Access control.
Only grant access to cardholders data on a need-to-know basis. Implement roles and permissions system and access control policy to make complying with this requirement more manageable.
8. Assigning unique identifiers to all users
Unique IDs, usernames and passwords for every user allow preventing hacks and tracing back any suspicious activity.
9. Physical access control
It’s crucial to protect cardholders’ data not only digitally but physically too. Servers, papers, and workstations should be thoroughly protected.
10. Monitoring and logging all access to sensitive data
PCI DSS requires keeping track of all data accesses. Monitor and log system activity for safety and accountability.
11. Testing your systems and processes for security
Regular security tests allow you to discover vulnerabilities before hackers.
12. Maintaining information security policy
Create and regularly update infosec policy, disseminating current versions company-wide. Third-parties that are somehow involved in your cardholders’ data processing should also read and accept this policy.
How to become PCI DSS compliant?
Here’s a brief PCI DSS compliance checklist for your reference:
- Analyse your current state and conformity to the requirements listed above.
- Use a self-assessment questionnaire designed for your business type to evaluate your preparedness. For large enterprises, a PCI DSS audit is needed.
- Tweak your environment to meet all the requirements.
- Ensure tokenisation of cardholders’ data.
- Fill in the attestation of compliance and wait for a qualified security assessor feedback.
- File all your PCI DSS documents to your card companies or banks and wait for their approval.
Check out our previous article, “Why do you need to be PCI DSS compliant?” for an extended checklist.
How much does PCI DSS certification cost?
The price of PCI DSS certification significantly varies depending on many factors, such as:
- Your business type and size. Some companies process much more cardholders’ data than others, and the cost of compliance for them grows accordingly.
- Your personnel and security culture. If you have Compliance and Security specialists on board, chances are they positively affect the way your team treats security. It lowers the cost of educating your employees and hiring external security consultants.
- Your setup. The price you’ll pay for compliance largely depends on your network design and technological environment.
Generally, the cost of PCI DSS compliance starts from around $300 annually for small merchants and exceeds $70,000 for large organisations. Resort to a Qualified Security Assessor for an accurate and detailed calculation of costs you’ll bear and a compliance process checklist tailored to your business specificities.




